 I’m absolutely baffled there isn’t more information out there about this. It seems like web managers and techs would be all over this, but there’s barely any information out there on this. I had a hard time finding documentation on OpenVPN’s site itself!
I’m absolutely baffled there isn’t more information out there about this. It seems like web managers and techs would be all over this, but there’s barely any information out there on this. I had a hard time finding documentation on OpenVPN’s site itself!
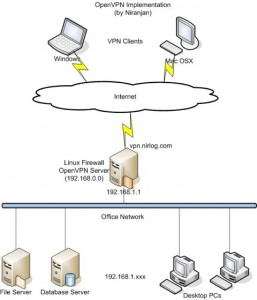
As one guy stated here (the post where I finally understood how this works) it’s not really “sharing” the port per se, but OpenVPN is deciphering between HTTP/S traffic and OpenVPN traffic and then forwarding web traffic over to another port, defined below. That’s crucial to understand.
Before I start, I want to note this doesn’t have to be done on an SSL port, as I understand it. I’m just using that as an example because it seems to be the most logical way to make it work if this is your configuration (you know, an SSL VPN going to an SSL port).
It should also be noted in this configuration example that OpenVPN, using the port-share parameter, is actually doing the listening on TCP port 443 and acting as a proxy itself that forwards non-OpenVPN traffic to the NGINX SSL port which we’ll layout below. You cannot do this utilizing UDP, that I know of.
So here’s what you do.
1) Set your NGINX or Apache listening ports. Set your NGINX standard http port 80 and SSL listening port to something OTHER than 443 … so, for arguments’ sake, let’s set it to 4443.
So it would look like this for Apache and NGINX:
For Apache, in the main httpd.conf (Windows) or in ports.conf (Ubuntu/Linux):
Listen 4443
For NGINX, in /etc/nginx/sites-available/defaults:
server {
listen 4443;
location / {
root /web/etc/blah;
}
}
Once implemented, restart your respective service, Apache or NGINX.
2) Next, you’re going to set your OpenVPN server parameters. Set your listening port to 443 from its standard 1194 and add the port-share parameter to point to the Apache or NGINX port created above. The config should look as follows now:
port 443
port-share 127.0.0.1 4443
proto tcp
OpenVPN will now be ready to accept connections over 443 and route the appropriate https/SSL traffic to Apache or NGINX.
3) Change your firewall settings. Leave your TCP port 80 rule pointing directly to Apache or NGINX. Then point your SSL rule to TCP port 443 running on your OpenVPN server. OpenVPN will now catch the traffic directed at it and decipher between OpenVPN traffic and HTTPS traffic.
4) Change the configuration in your OpenVPN clients. Point your OpenVPN clients to TCP port 443 instead of the port you were using before:
remote domain.name.com 443
or
remote [IP ADDRESS] 443
Hope it works. Cheers!