Documenting settings to get IPv6 setup within the configuration for OpenVPN, plus forwarding all IPv6 traffic through the VPN. This has no explanation of how you obtain IPv6 address prefixes frrom your ISP or how it works differently from IPv4, just simply how to get it working within OpenVPN. Will update if needed.
Category: Technology Page 2 of 17
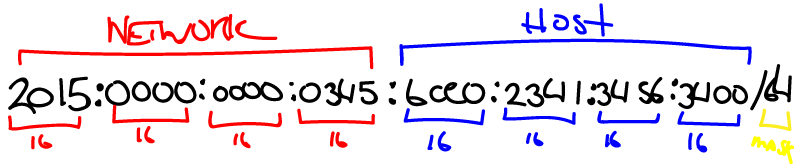
Update: for a newer version of this information set within the Config Tree portion of the web interface of the EdgeRouter 4, read this post, with pictures and all! 🙂 https://davidwesterfield.net/2021/03/enabling-ipv6-prefix-delegation-on-att-internet-for-a-second-firewall/
I’m archiving this information for future reference because I (or others) may need it. This was extremely helpful in getting AT&T’s allotted IPv6 subnet(?) (properly called: delegated prefix) setup in my EdgeRouter 4, although I wound up having to use the web interface and configuring the same settings within the Config section. Without further ado (or a whole lot of ado below) here is Bradley Heilbrun’s explanation.

From the Westminster Larger Catechism. I’m still learning how all of this applies in the realm of social media engagement specifically and desire to walk this way (albeit imperfectly).
Q. 144. What are the duties required in the ninth commandment?
A. The duties required in the ninth commandment are, the preserving and promoting of truth between man and man, and the good name of our neighbor, as well as our own; appearing and standing for the truth; and from the heart, sincerely, freely, clearly, and fully, speaking the truth, and only the truth, in matters of judgment and justice, and in all other things whatsoever; a charitable esteem of our neighbors; loving, desiring, and rejoicing in their good name; sorrowing for and covering of their infirmities; freely acknowledging of their gifts and graces, defending their innocency; a ready receiving of a good report, and unwillingness to admit of an evil report, concerning them; discouraging talebearers, flatterers, and slanderers; love and care of our own good name, and defending it when need requireth; keeping of lawful promises; studying and practicing of whatsoever things are true, honest, lovely, and of good report.
Q. 145. What are the sins forbidden in the ninth commandment?
A. The sins forbidden in the ninth commandment are, all prejudicing the truth, and the good name of our neighbors, as well as our own, especially in public judicature; giving false evidence, suborning false witnesses, wittingly appearing and pleading for an evil cause, outfacing and overbearing the truth; passing unjust sentence, calling evil good, and good evil; rewarding the wicked according to the work of the righteous, and the righteous according to the work of the wicked; forgery, concealing the truth, undue silence in a just cause, and holding our peace when iniquity calleth for either a reproof from ourselves, or complaint to others; speaking the truth unseasonably, or maliciously to a wrong end, or perverting it to a wrong meaning, or in doubtful or equivocal expressions, to the prejudice of the truth or justice; speaking untruth, lying, slandering, backbiting, detracting, talebearing, whispering, scoffing, reviling, rash, harsh, and partial censuring; misconstructing intentions, words, and actions; flattering, vainglorious boasting, thinking or speaking too highly or too meanly of ourselves or others; denying the gifts and graces of God; aggravating smaller faults; hiding, excusing, or extenuating of sins, when called to a free confession; unnecessary discovering of infirmities; raising false rumors, receiving and countenancing evil reports, and stopping our ears against just defense; evil suspicion; envying or grieving at the deserved credit of any; endeavoring or desiring to impair it, rejoicing in their disgrace and infamy; scornful contempt, fond admiration; breach of lawful promises; neglecting such things as are of good report, and practicing, or not avoiding ourselves, or not hindering what we can in others, such things as procure an ill name.
“For the first time in a long time, I believe that we can speak the words of truth into an issue that can have true and lasting effects on how tools like AI are developed and used in our world. The benefits of this technology are great, but the dangers are real. Just as electricity changed everything about our society, AI is due to change even more in a shorter period of time. We are entering a new age of AI where everything about your life and our communities will be different. The church has the unique opportunity and obligation to speak boldly to a watching word with a word of hope and peace that who you are is not tied to what you do, rather your dignity is tied to the One that created the entire world. No matter how advanced AI might become in the future or how dependent our society already is on the technology, nothing can change who you are as an image bearer of God. This guiding ethic drives everything we do as Christians and has life-altering applications to the issues that AI is presenting to our homes, communities, and world.”
After working through a number of WordPress sites over the years and either preventing hack attempts or intervening in cleaning up hacked sites, I’ve “engineered” a free way to keep your site secure with the use of these plugins in conjunction:
- iQ Block Country: This plugin will prevent certain countries that you set from accessing either the front-end of your site, or (in the cases I use it for almost exclusively) the back-end. For the purposes of the sites I manage, I block all except the United States on the back-end and leave the front-end open to all.
- Jetpack: this is a great plugin to utilize anyway just for stats collection, image/CDN offloading, but included within this plugin is the ability to turn on brute force login protection. Another very helpful prevent if these other tools don’t catch something.
- WordFence: this free tool (that actually does have a subscription service for even better protection) is a web application firewall for use directly within WordPress. One of the big things it prevents are brute force login attacks, XSS attacks and SQL injection attacks, amongst others. Now, a web app firewall (like ModSecurity or some other hardware appliance like a Barricuda or Cisco firewall) in front of the application itself would work even better at preventing attacks before they even got to your WordPress site (if setup correctly), but can be quite advanced to install and configure. Regardless, this plugin is a great way to keep those kinds of attacks at bay.
- Invisible reCaptcha: this utilizes the newer version 3 of Google’s reCaptcha to prevent automated bots from either spamming the comment sections of your posts or pages or from brute force attempts to login to your site as admin.
None of these methods are fool proof from attacks getting through some other threat vector, but I’ve found this to catch quite a bit of junk on all the sites I’ve set them up on.
And one last thing: make sure and secure your site with SSL?!? 🙂
In the course of attempting to find a good, fast solution to running backups from my Linux server to my laptop for all the important stuff, I worked through the ability to run rsync on my Windows laptop using the cygwin environment, bash scripts and scheduling the backups to run in Task Scheduler. Here’s a run down of the steps I went through:
The following commands enable, follow in real-time and disable the querylog entries for when you’re trying to troubleshoot or watch the connection.
1. Enable: sudo rndc querylog
2. Follow: sudo journalctl -f
3. Disable: sudo rndc querylog
This is a fascinating article about the underpinning and foundation of China’s surveillance and social credit system and the systems engineering theories and methodologies that brought it about. I find it particularly interesting the author specifies the use of “carrots” (means of pleasure, getting at the desires and loves of the populace) and “sticks” (means of coercion, inflicting punishments on the populace for stepping out of line) to essentially control the masses. This has roots (though not one for one) in some things Aldous Huxley said in a lecture at Berkeley in the 1960’s about “scientific dictatorships” of the future. It’s worth listening to:
https://archive.org/details/AldousHuxley-TheUltimateRevolution
“The average American teenager who uses a smart phone receives her first phone at age 10 and spends over 4.5 hours a day on it (excluding texting and talking). 78% of teens check their phones at least hourly and 50% report feeling ‘addicted’ to their phones. It would defy common sense to argue that this level of usage, by children whose brains are still developing, is not having at least some impact, or that the maker of such a powerful product has no role to play in helping parents to ensure it is being used optimally. It is also no secret that social media sites and applications for which the iPhone and iPad are a primary gateway are usually designed to be as addictive and time-consuming as possible, as many of their original creators have publicly acknowledged.”
https://thefederalist.com/2018/01/10/apple-facebook-arent-going-save-us-smartphone-addiction/
From an interview with James Cameron, director of the Terminator and Alien movies, amongst many others, and Tim Miller.
